
by Deijah Price | Feb 9, 2022 | Metaverse
If you wish to experience the fullness of the Metaverse, cryptocurrency is crucial. Many applications are built on blockchain technology and the metaverse is typically decentralized. Decentralization refers to the fact that the Metaverse isn’t governed by a central...

by Esam Nimer | Jan 7, 2022 | Blog
Many organizations, small to large, have outsourced IT and other vital business functions to third-party vendors. Outsourcing various functions to third-party vendors allows organizations to focus on core functions and areas of expertise, while reducing business costs...

by Perry Lynch | Nov 1, 2021 | Blog
An almost universal truth in small to mid-sized enterprise environments is that IT and Security departments are small in size and are faced with a wide array of responsibilities. In regulated industries, key responsibilities include supporting or enforcing compliance...

by Esam Nimer | Oct 5, 2021 | Blog
2020 was an unprecedented year for all industries and cybersecurity was no exception. It was a record-breaking year for data breaches and number of cyber-attacks, with the average cost of a data breach reaching $3.86 million. The number of cyber-attacks and data...
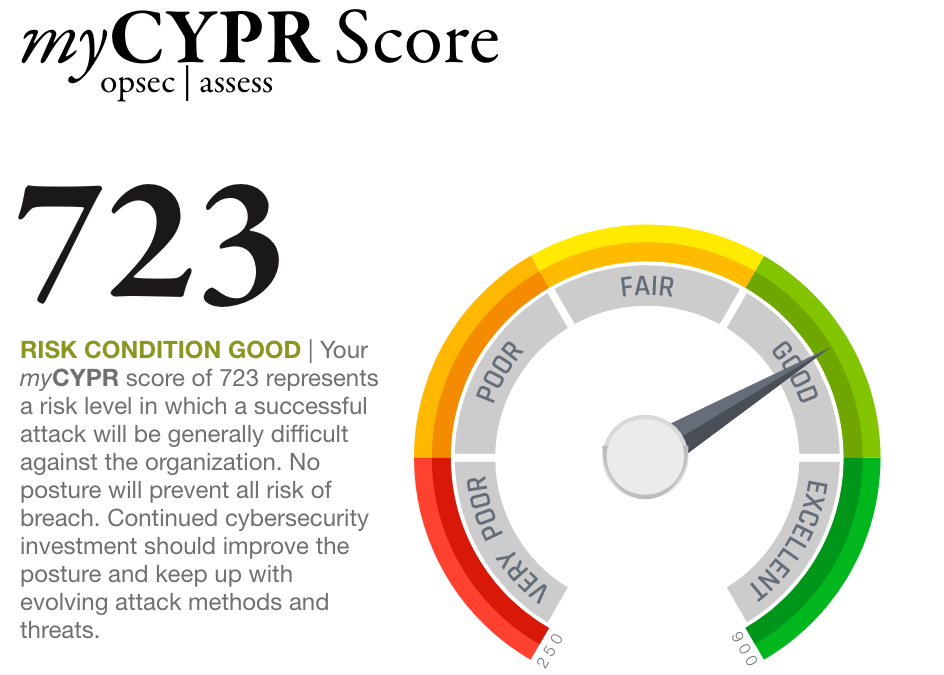
by Meagan Huebner | Jun 10, 2021 | Blog, Security Ratings, Third-party risk management
If you’re familiar with a credit score, you already have a better understanding of cybersecurity risk ratings than you think. A credit score is a quick and easy way to tell lenders about your creditworthiness, providing a prediction of how likely you are to pay back a...

by Esam Nimer | May 27, 2021 | Blog
Strengthening physical security could stop an attack before it happens and potentially save your organization from significant financial damages. Physical security is the protection of people, property, and physical assets from different actions and events that could...







